Summary:
What the mid-1990’s debate about the so-called “clipper chip” can teach us about our contemporary debates concerning NSA surveillance of the Internet and the Web.
Listen:
This episode was originally written as a piece on Medium, entitled The NSA Tried This Before, What The 90s Debate Over The Clipper Chip Can Teach Us About Digital Privacy, which I’ll republish below, complete with my original links for context.
We’ve Been Down This Road… Something Something… Forgetting History… Something Something… Doomed To Repeat It
There is a concern that the Internet could be used to commit crimes and that advanced encryption could disguise such activity. However, we do not provide the government with phone jacks outside our homes for unlimited wiretaps. Why, then, should we grant government the Orwellian capability to listen at will and in real time to our communications across the Web?
If I showed you to quote on the left, and gave you no attribution for it, you’d be forgiven for assuming it was recent. Logically you might assume that the quote came from a privacy crusader, angered by the Snowden revelations and agitating to protect our civil liberties online.
The truth is, the quote is about opposition to an NSA-sponsored surveillance initiative.
But the quote comes from 1997. And it comes from none other than John Ashcroft.
Over the course of my research for this Internet History project, over and over again, I’ve run across references to the debate in the early 1990s about the so called “clipper chip.” This was an initiative by the NSA… supported by the Clinton administration… that would have inserted an encryption chip with a government “back door” into every phone and electronic communication device manufactured. I have just a vague recollection of the issue from the time, but looking back 20 years later at the fierce debate that surrounded the clipper chip is both bizarre (Ashcroft, and other Republicans who would go on to oversee the implementation of things like STELLAR WIND after 9/11 were at this time opposed to NSA spying!) and edifying (the clipper chip debate was perhaps the first time the digital community rose up in defense of their rights.)
Given the state of our current debate about government surveillance of communications and our online lives, I thought it would be instructive to look back at the clipper chip debate and see what lessons we could glean from it. Long before the fight against PIPA and SOPA, this was the first time that citizens of the net rose up and proved they were a constituency that mattered. After all, the clipper chip was defeated.
At least, we think it was…
It Was A Simpler Time…
… at least, in terms of technology.
Back in the early 1990s, the Internet was just going mainstream. The web had only recently been born. And those few million Americans who were going online largely did so by dialing in to places like American Online and Prodigy.
But the country was primed for some kind of technological revolution. Magazines and newspapers were hyping a new digital future they dubbed the “information superhighway.” In a previous episode of the podcast, I laid out how the Information Superhighway and the Internet were two entirely different phenomena. But the Internet rose to prominence soon after the Info-Bahn hype, so most people assumed they were the same thing.
The administration of Bill Clinton and Al Gore had won office in part by championing the promise of technological investment as a way to overcome the post-Gulf War I recession. Clinton, and Gore especially, seemed to be plugged into the vanguard of a new tech utopianism. It was the time of the launch of Wired magazine; of the Mosaic browser; of freeware and shareware. The techno-counterculture felt itself ascendant, ready to usher in a transformative new age which the neo-laissez-faire Clinton administration seemed eager to encourage.
Which is why it was so shocking when, in 1993, news of the Clipper Chip leaked out. It seemed the promise of cyberspace would be corralled and caged before it could even get going. What was worse, it wasn’t Microsoft that would be the jailer. It would be the US Government.
“Key Escrow”
Into the midst of this early tech euphoria, waded the National Security Administration. At the time, the NSA was the less well-known sibling of the CIA, tasked since the Truman administration with the code-making and code-breaking aspects of the espionage game. The NSA was less familiar because, up until the Church hearings of the 1970s, the US Government had never officially acknowledged the existence of the NSA. Until that time it was euphemistically referred to as “No Such Agency.” But at this point in time, computers were beginning to take over our lives. In 1993, only 22 percent of American households owned a computer, but that would more than double in a few short years. And computers had made great inroads in corporate America. And the general telecom revolution was starting to hit its stride as well. Cellular telephony was on the horizon. The great technical innovations of the day were fax machines and cordless land-line telephones.
The powers-that-were in law enforcement and national security were concerned. More and more of the world’s daily business was moving away from realms that were conducive to monitoring by traditional methods such as wire-tapping, bugging and sifting through people’s trash. Now things were done via ones and zeros, zipping around the world at the speed of light. It wasn’t that the new electronic means of communication were secure. Far from it. If you’ll recall, it was ridiculously easy to eavesdrop on people’s cordless telephone conversations, as Prince Charles and Princess Diana both so famously discovered.
But in this new digital realm, there was a great solution to the problem of privacy: encryption. If it was digital, it could be encrypted and it could be encrypted in a way that even for the government, might be unbreakable. Thus, the NSA found the role and the relevancy that it perhaps was born for. And this is perhaps our first great lesson from history: The NSA first became interested in the digital world because it feared encryption. Encryption means unbreakable codes. Remember, breaking codes is the NSA’s jam.
And so a second key point to realize here is that in terms of eavesdropping and surveillance, listening in to old-style wired communications and radio transmissions really isn’t that difficult, technically speaking. But breaking into digitally encrypted communications is orders of magnitude harder. Especially in the era of powerful computers, once you put information into digital form, the math is such that there is a very real possibility that you will never break the code. Innovations such as public key cryptography, digital signatures and the RSA algorithm would, by the 80s and 90s, lead to the protocols such as SSL, which make the modern internet possible. (One of the many reasons people were initially skeptical of the viability of e-commerce was because they feared a sufficient level of security could never be achieved) And so, those in the surveillance community were worried that once the majority of communications entered the digital domain, and thus the domain of math, the snoops and surveillors of the world might be frozen out, possibly forever. Theoretically unbreakable encryption could be employed to lock down communications.
Clearly, the NSA was one of those aware of this looming problem, and they were worried they might soon be unable to do their job. So they decided to get ahead of the issue, before they were locked out of the coming wave of digital communications.
Thus the NSA began circulating a proposal in early 1993 to create the technology that would eventually have the name “clipper chip.”
The idea was basically that, in the factory, every new piece of electronic hardware produced would be equipped with a chipset that would allow standard cryptography to take place and shield communications from third-party eavesdropping. The encryption would function as intended, but there would be one big caveat… By design, a 3rd “key” would exist in every chipset. This key would be held “in escrow” by the government. If the government could prove (for example, via a traditional warrant, okayed by a judge) that the communication in question needed to be un-encrypted for the purposes of law enforcement, then the third key could be used to unlock everything.
Initially, the proposal emphasized that the clipper chip would be voluntarily added to phones, as that was the dominant means of communication, even at that time. But clearly, the scheme could be implemented in the manufacture of computers, fax machines, pagers and the like further down the road.
I’ll leave it to the experts at the Crypto Museum to explain the technical details:
The Clipper Chip used the Skipjack encryption algorithm for the transmission of information, and the Diffie-Hellman key exchange algorithm for the distribution of the cryptographic session keys between peers.
The Skipjack algorithm was developed by the NSA and was classed an NSA Type 2 encryption device. The algorithm was initially classified as SECRET, so that it could not be examined in the usual manner by the encryption research community. After much debate, the Skipjack algorithm was finally declassified and published by the NSA on 24 June 1998 [2]. It used an 80-bit key and a symmetric cipher algorithm, similar to DES.
What is fascinating about this proposal, at least in retrospect, is that it was proposed publicly. Again, maybe it was a simpler time. Or maybe the NSA thought that the logic of their argument would carry the day. Essentially, the proposal made the point that: in the future, we fear that our traditional surveillance tools might be rendered inoperative. In preparation for that day, let’s all agree to voluntarily move the existing surveillance apparatus into the future. It will be just like wire tapping, but now online! We’ll still have to go to a judge and get permission to listen in, but that’s what we already have to do. This will allow us to essentially do the same thing. But before we can do so, we have to bake-in this hardware component first, or we’ll be back at square one.
The logic of the argument certainly convinced the Clinton administration, which, in February 1994, announced support for the clipper chip initiative. And some security and law enforcement experts concurred, clearly fearing that technology was about to bring on a surveillance apocalypse. Here is the New York Times from June of 1994:
If something like Clipper is not implemented, writes Dorothy E. Denning, a Georgetown University computer scientist, “All communications on the information highway would be immune from lawful interception. In a world threatened by international organized crime, terrorism and rogue governments, this would be folly.”
It’s impossible to understate how much the widespread use of cryptography, that computers and digital technology made possible, was the NSA’s Armageddon scenario. Again, from that same New York Times piece:
That was the National Security Agency’s greatest nightmare. Every company, every citizen now had routine access to the sorts of cryptographic technology that not many years ago ranked alongside the atom bomb as a source of power. Every call, every computer message, every fax in the world could be harder to decipher than the famous German “Enigma” machine of World War II. Maybe even impossible to decipher!
And so… how civil of them! They seemed to be taking their greatest problem to the public and asking them… voluntarily… in the interests of national security… to go along with solving it for them. The implicit promise seemed to be that the new system would operate just as the old system had. Judicial oversight. Warrants. We have to get permission to utilize that 3rd key held in escrow!
Except… a lot of people didn’t see it that way. The clipper chip quickly attracted a firestorm of controversy.
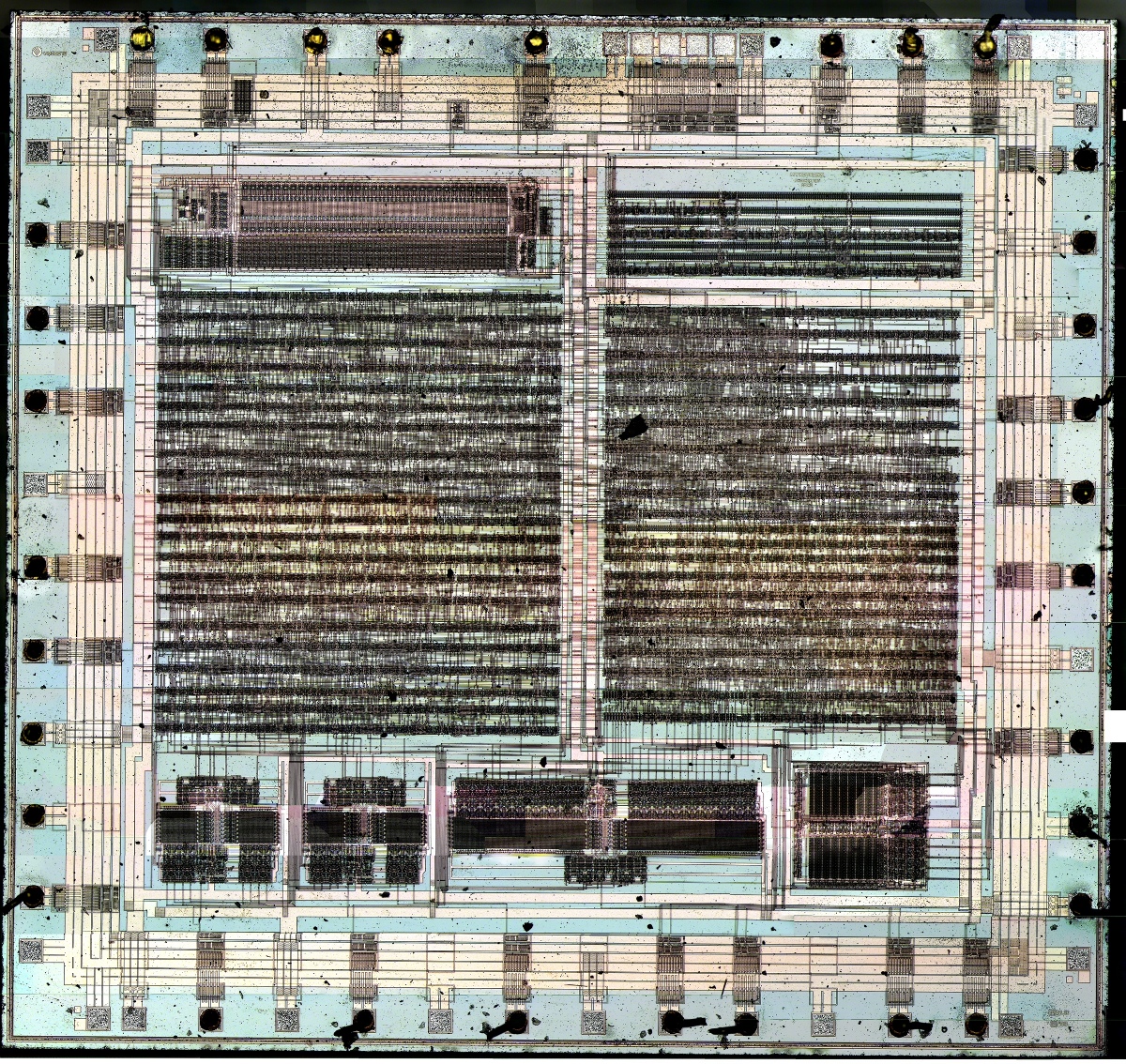
For one thing, industry was wary. The whole thing certainly seemed heavy handed. The government wanted the right to insert something into every product that private industry made. That feels icky even today, but in 1994 if felt downright draconian. Participation in the clipper chip hardware program was supposed to be voluntary, but private enterprise saw Big Brother everywhere. The only telephone (and to my knowledge, the only piece of hardware ever produced with the clipper chip inside) was the TSD-3600 developed by AT&T. The image at the top of this article shows the clipper chip, known as MYK78T, manufactured by a company named Mykotronx.
It was “voluntary” but also costly. An un-programmed chip reportedly cost $16 and a programmed one cost $26. Who wanted to pass that on to the consumer “voluntarily?”
Industry was also concerned that adopting this sort of device would put American technology at a disadvantage in the global marketplace. With echoes of the current debate about how NSA spying has “broken” trust in Silicon Valley, companies argued that foreign consumers and corporations would not want to buy American electronics with a clipper chip in them. After all, the escrow key was only in one entity’s hands: Uncle Sam. Why would a German or a Chinese businessman buy a phone that Uncle Sam had the un-lock key for?
But the opposition was also a product of the times. This was 1994. The time of the Republican “tidal-wave” against the administration of Bill Clinton. This was the era of the Contract With America. This was Ruby Ridge. And Waco. And Janet Reno. I hope I’m not carving out any sort of partisan stance when I state that the party out of power always tends to rediscover its faith in civil liberties. And thus, Republicans (along with some Democrats) came out strongly against the clipper chip initiative.
Again, let’s return to this John Ashcroft speech, which was made some years after the debate had died down, but exemplified the Republican opposition to the scheme. Ashcroft was considered the “go-to” point man in Congress for opposition to the clipper chip.
The Clinton administration would like the Federal government to have the capability to read any international or domestic computer communications. The FBI wants access to decode, digest, and discuss financial transactions, personal e-mail, and proprietary information sent abroad — all in the name of national security. To accomplish this, President Clinton would like government agencies to have the keys for decoding all exported U.S. software and Internet communications.
This proposed policy raises obvious concerns about Americans’ privacy, in addition to tampering with the competitive advantage that our U.S. software companies currently enjoy in the field of encryption technology. Not only would Big Brother be looming over the shoulders of international cyber-surfers, but the administration threatens to render our state-of-the-art computer software engineers obsolete and unemployed.
And of course, Ashcroft himself, just a few years later, would be part of an administration that would–after 9/11–implement a policy that would do all of the above.
The Grassroots Rise Up
But it wasn’t just Republican Senators and telecom companies that were discomfited by the clipper chip. The nascent digital rights movement was quick to seize upon the clipper chip as a call to arms. Organizations like the Electronic Frontier Foundation, the Electronic Privacy Information Center and the Center For Democracy and Technology had been formed in the 90s partially as a way to protect hackers and rebrand hacking as a potentially legitimate endeavor. But they were quick to pivot and tackle the clipper chip threat as well. These groups, along with the ACLU, joined forces to challenge the legality of the chip, saying that is was more like key surrender rather than key escrow. EFF co-founder John Perry Barlow told Time magazine, “You can have my encryption algorithm when you pry my cold dead fingers from my private key.” A group called Computer Professionals for Social Responsibility gathered tens of thousands of signatures via email, one of the first times the Internet was used for this kind of awareness-raising and advocacy. A group called the Cypherpunks met regularly in silicon valley to devise code that would preemptively break the clipper chip, or else, render it useless. And indeed, efforts like this led to the development of a whole new generation of encryption packages like Nautilus, PGP and PGPfone. The hope was that if the public adopted enough of these packages, the clipper chip could be crippled out of the gate.
Over the course of 1994-1996 the young Internet community rose as one to defeat what they saw as a threat to their lifestyle. Among the generation of computer nerds and geeks that had spent the 70s and 80s imagining all the ways digital technology would transform society, there was a tangible sense that it was all finally happening. The long promised cyberpunk future was now. They were not about see everything ruined right at their moment of triumph. And let’s not forget the unique mishmash of culture that the Internet and the web grew out of. Early Internet culture was a weird hybrid of 60’s San Francisco hippie-dippy-ism, meshed with MIT-scientist-Libertarianism. This was an era when shareware was more common than pay software on the net; when advertisements and commercialism on the web were seen as a betrayal of core-values. The Anarchist Cookbook was freely traded on Usenet groups alongside pornography and cracked copies of Doom. Silicon Valley is a place that has always embraced the ideas of the Whole Earth Catalog and Peter Thiel in equal measure.
So, an odd combination of industry, congressional and hacktivist pressure combined to defeat the clipper chip. It helped that industry leaders from Apple to Netscape came out against the proposal. It also helped that a young computer scientist at Bell Labs figured out the clipper chip was easily spoofed. The chip proposal was never formally dropped (the Clinton administration made several revised attempts to launch the proposal in modified formats) so much as it was quietly forgotten. Again, I think it was a combination of factors unique to the time period that helped sink the clipper chip. On the one hand, Republican fear of Clinton-style big-governmentism generated a meaningful a political energy for opposition. And at the same time, the administration was already beginning to see that, indeed, Silicon Valley-led technological innovation could and would bring about an unprecedented era of creativity and prosperity. There was a bit of not wanting to look a gift horse in the mouth about the whole thing. In addition, this entire topic was new-fangled and confusing to the non-tech-minded politicians. If the geeks said this policy was bad for technology development overall, the pols were willing to take their word for it.
The NSA’s Game Is The Same As It Ever Was
When you look back at this debate in the context of what we know now, it’s obvious that the NSA has had one motivation this entire time. Ever since society has moved in a digital direction, they have been living in fear of being rendered redundant. They know that unbreakable encryption is possible in a digital world and as more and more aspects of everyday life are being lived online, they fear a day will come when they are completely blind and impotent. The clipper chip was an attempt on the NSA’s part, possibly in good faith, to come to an accommodation with a digital society. We would be allowed to do our surfing and out chatting, if only we would be so kind as to leave a back door open for the NSA to do their job of monitoring us. But we rejected this polite proposal, and so we have to assume that the NSA simply resolved to stop asking for permission.
It would only be five short years between the time that the debate about the clipper chip died down (in 1996)… and the events in 2001 that would inspire the laws that would give the NSA the legal fig leaf to do what they’ve always wanted to do.
This is, I think, the key insight that looking back at the clipper chip debate gives us. A lot of us tend to think of the NSA as this all-powerful, voracious and rapacious entity seeking to monitor and possibly control our lives. We feel like they want to record everything we do because they are on a mad power trip. But from an equally probable perspective, the NSA is an agency running scared. The wired world is their worst nightmare. In the past, only a tiny fraction of the world’s business was done behind the closed doors of encryption. But now it’s all ones and zeros and the NSA knows that the math is always out there to create encryption systems that they can’t break into. From their perspective, complete disaster is always right around the corner, and it has been since the early 90s.
What we now know about the NSA’s behavior bears this out. The clipper chip was just their first gambit, but the goal has always been the same: to poke enough holes in encryption systems to keep their capabilities intact. As Paul Kocher, one of the designers of the SSL protocol told the New York Times, the failure of the clipper chip was, at best, just a bump in the road, “…they went and did it anyway, without telling anyone… The intelligence community has worried about ‘going dark’ forever, but today they are conducting instant, total invasion of privacy with limited effort.”
Thanks to Snowden, we know that around the year 2000, with initiatives like Project Bullrun, STELLARWIND and others, the NSA has been pressuring technology vendors to install backdoors in their products that the snoops can exploit. Going to Google and Facebook and demanding to tap their servers is just like asking AT&T to “voluntarily” install clipper chips in phones. But nowadays, cooperation is even not remotely voluntary. The NSA isn’t asking. The law is such that you have no choice but to cooperate. And the NSA is not above stealing tech or covertly inserting vulnerabilities behind a vendor’s back. We also know that the NSA is perfectly comfortable exploiting security vulnerabilities, even at the expense of the health of the wider web. It’s little wonder that the same debates that surfaced around the clipper chip are coming to the fore once again.
- Doesn’t this level of insecurity just serve to make us all a little bit less safe? If the NSA is going around purposefully breaking things like SSL, then sure. In the name of national security, our banking systems could be compromised.
- Isn’t a surveillance regime like this just ripe for abuse? Um… Yes.
- Couldn’t this ultimately cost silicon valley its reputation, and thereby its lead in technology and profits? Almost certainly.
These were all precisely the arguments that scuttled the clipper chip. It’s just that in the wake of 9/11, there was no room for debate about the possible ramifications. The NSA was simply given the blank check to create the apparatus they always wanted. And steps one through seven of that apparatus were about making sure that impenetrable cryptology would forever be kneecapped.
The NSA hoovers up every bit of data because it’s so easy to do so and simply because it can. In the New York Times article from 1994, it mentions that in all of 1993, only 919 Federal, state and local taps were authorized. Those were ALL the authorized surveillance operations in the entire country. And that was back in the technologically simple days of wiretapping. In 2012, there were 1,789 surveillance requests and 15,229 National Security Letters presented to secret FISA courts. So clearly, there’s more they want to look at these days. And that’s only the stuff they ask to look at.
But the actual surveillance is always secondary to the prime directive of ensuring that the surveillance is possible. That the backdoors and the exploits are there. That truly secure encryption is a mirage just beyond us on the horizon.
And maybe that’s what we should keep in mind as the debate about our national security and government surveillance moves forward.
It’s unlikely that we can replicate the political environment that killed the clipper chip in the 1990s. Once again, it’s the Democrats who are in power and in bed with Big Brother, but the Republicans don’t seem to be all that concerned about it. The generation that runs Silicon valley these days seems a far cry from the hybrid hippie/libertarian generation that founded the web. If anything (cough… Zuckerberg… cough) they view privacy as a weird anachronism.
Certainly, there is still a movement to preserve our digital civil rights. And some corporations seem to be just as offended by governmental overreach as we are.
But if we’re really going to reclaim the net from the NSA and other Orwellian bad-actors, maybe we just have to keep in mind that it’s the power of the Internet itself the NSA fears. Bulletproof encryption is always possible, we just need to rebuild an infrastructure that makes it workable. The NSA has been struggling to bottle the genie of digital encryption for 25 years now. And they know that either one of two outcomes are possible: either everything in modern life will be on the net, permanently traceable, catalog-able and recorded… or else, everything in modern life will be on the web but it will be opaque.
Footnote
I started this piece with a quote from John Ashcroft, who was a member of the administration that presided over the implementation of the current NSA surveillance regime. And yet, some of you might remember the story about how, from a hospital bed, Ashcroft himself refused to authorize some specific surveillance measures he felt were a bridge too far.
I’ll let ArsTechnica take it from here:
The infamous showdown took place in March 2004, while Ashcroft was recovering from illness in a hospital bed. Acting attorney general James Comey—now President Obama’s nominee to head the FBI—was refusing to reauthorize one component of the secret surveillance program. Comey concluded that it was illegal. This prompted White House counsel Alberto Gonzales to rush to Ashcroft’s hospital room in hopes of getting the ailing AG to countermand Comey, who was tipped off about Gonzales’ plan and sped there as well.
In the confrontation that ensued, Ashcroft supported Comey both formally (because Comey was legally the attorney general while Ashcroft was incapacitated) and on the legal substance. Bush reauthorized the program despite the Justice Department’s conclusion that it was unlawful. Comey then threatened to resign—with Ashcroft, FBI director Robert Mueller, and other top officials reportedly ready to join him. Bush ultimately backed down, and the troublesome program was briefly suspended until it could be renewed under a different legal authority.
In 2008, we learned that the central bone of contention during this showdown wasn’t warrantless wiretapping but rather some form of data mining. More recently, via reporting in The Washington Post and a classified NSA report leaked by The Guardian, we learned that the controversy specifically involved Internet—not telephone—metadata.
So, it seems that, however briefly, Ashcroft regained the conscience that had once enabled him to voice the words I quoted at the beginning of this piece.
Maybe we just need other people in government to find their consciences in similar ways.













[…] Indeed, the Clinton administration followed through with various bills to this effect. And in fact, Gore himself was often involved in many internet and web firsts. Gore became the first Vice President to give a live interactive news conference on a computer network. The first ever White House website was launched as early as October 21, 1994, two months before Netscape version 1.0 was even launched. As a part of Gore’s high-profile project to streamline government bureaucracy, Federal Government agencies were encouraged to utilize the web and internet to cut down on waste and redundancy. And then there was Gore’s involvement in the infamous Clipper Chip initiative, which I discussed in another episode of this podcast. […]